Did you know that 91% of all cyber attacks start with a phishing email?
This astonishing figure underscores how important strong email security is. DKIM, or DomainKeys Identified Mail, is one of the best defenses against these kinds of attacks since it verifies that emails received from your domain haven’t been altered in transit.
Securing these conversations becomes not just prudent but necessary in the digital world when email communication is fundamental.
An important technique used by cybercriminals—email spoofing—is greatly reduced by DKIM. How? It adds a level of protection that confirms an email really came from the domain it claims to represent.
This guide provides a comprehensive introduction to DKIM to help you protect your communications in an increasingly dangerous digital world. We’ll examine its significance in your email security plan and walk you through setting it up for Microsoft Office 365.
Understanding DKIM
Email spoofing is one of the security hazards that DomainKeys Identified Mail (DKIM) aims to assist protect against.
DKIM primarily verifies for the recipient whether an email claiming to originate from a particular domain was indeed approved by the domain’s owner.
Q: What is email spoofing and how does it affect deliverability?
A: Email spoofing is when a sender fakes the “From” address in an email so it appears as if it’s coming from a trusted source. This is used for phishing or spam, and it can drastically harm your email deliverability. When ESPs detect spoofing, they may block or mark the email as spam—damaging the sender’s reputation and reducing the chances of future emails reaching the inbox.
How DKIM works
- Signing the email. The sender’s email server securely holds the private key used to sign when sending an email. This digital signature, attached to the email’s header, is unique to each email.
- Verifying the signature. The public key, which is published in the DNS (Domain Name System) records of the sender’s domain is then used by the receiving email server to decrypt the signature. This allows it to authenticate the sender of the email, and ensure that the email was not tampered with while it was in transit.
- Authentication result. Successful verification proves that the email was sent from the domain it’s claiming to be from, and that the contents haven’t been tampered with. This result is then generally returned to the recipient’s email client, which then decides how incoming emails are processed (e.g. whether or not the email should be considered trusted or sent to spam).
Importance of DKIM
The benefits of implementing DKIM include a greater sense of security around what to expect with emails and a reduction in phishing-type messages. The same holds true for the application of DKIM, with increased chances that a third-party service provider will identify the intended sender of an email as the legitimate sender rather than a spam creator. Thus, this is an action that can be taken for both parties involved since it strengthens proper delivery and spam avoidance. Trust is the foundation of all communication, and since email is one of the most common ways to communicate, it is almost taken for granted these days.
Prerequisites for setting up DKIM in Office 365
Before you go ahead and implement the configuration of DKIM of Microsoft Office 365, there are some requirements you need to ensure are met:
- Admin access. If you have one or more Office 365 installations where you do not have administrative access, you will not be able to configure DKIM settings.
- Domain setup. Verify that Microsoft 365 has properly added and validated your domain. This entails configuring your domain so it can send and receive emails and adding it under your Office 365 account.
- DNS access. DKIM is based on CNAME records, so you must have access to modify the DNS records of the domain you plan to configure DKIM for.
Step-by-step guide to configuring DKIM for Office 365
Configuring DKIM (DomainKeys Identified Mail) with Office 365 is a vital step in securing your emails. Follow this configuration guide:
Step 1: Launch the Office 365 admin center
- First log into your Microsoft 365 admin center. You’ll need admin permissions to reach the necessary settings.
- Visit admin.microsoft.com and enter your credentials.
Step 2: Locate the DKIM configuration settings location
- In the Microsoft 365 admin center, navigate to the Exchange admin center. You can access it from the admin centers section >> Exchange.
- In the Exchange admin center, go to Protection, and then select DKIM. In this section, you can control and configure DKIM settings for your allowed domains.
Step 3: Set up DKIM DNS records on your domain
Choose the domain you want to use DKIM for, and choose to create the DKIM keys. It will create 2 CNAME records that you have to publish in your DNS. This is what these CNAME records usually look like:
Record for Selector 1:
- Host name (Name/Host/Alias):
selector1._domainkey.yourdomain.com - Points to (Value/Answer/Destination):
selector1-yourdomain-com._domainkey.yourdomain.onmicrosoft.com
- Host name (Name/Host/Alias):
Record for Selector 2:
- Host name (Name/Host/Alias):
selector2._domainkey.yourdomain.com - Points to (Value/Answer/Destination):
selector2-yourdomain-com._domainkey.yourdomain.onmicrosoft.com
- Host name (Name/Host/Alias):
These records are crucial as they are used to verify the DKIM signature of outgoing emails from your domain.
Learn more here: Everything You Need to Know About DKIM Selector: What Is It and How to Find It?
Step 4: Setup DKIM signing for your Office 365 emails
- Once you add the CNAME records to your DNS, return to the DKIM settings in the Exchange admin center.
- Choosing the domain you want, set DKIM signing to enable. Enabling this feature can take some time based on your DNS provider.
- Ensure the DNS records are propagating before you enable it.
Additional considerations
- DNS propagation. It may take up to 48 hours for changes to DNS to propagate. Once you have verified that DNS records are correct and have already been propagated, only then should DKIM signing be enabled. Learn more about DNS propagation here.
- Verification. After enabling DKIM, it is a best practice to check if it’s working properly. There are many online tools you can use to check the DKIM record.
- Troubleshooting. Where DKIM is not enabled, check the syntax and presence of your CNAME records in your DNS set up. Another option is to verify missed errors by referencing Microsoft’s support resources or your DNS provider.
Troubleshooting common DKIM setup issues
- If DNS records are incorrect—ensure DKIM CNAME records are entered as recommended via the Office 365 admin center. This is a common error as many people enter them on their own instead of using the values given for your domain, and it’s an easy fix.
- Don’t worry about DKIM failing or failing DKIM DNS records if the DNS records don’t change right away. Give it 48 hours and then check your DNS lookup again. DNS records can take approximately 48 hours to propagate, and once yours are propagated to other DNS servers, everyone else will be able to locate the DKIM records, too.
- With DKIM signature failures, check if the email is modified after signing—subject lines, capitalization, or even removing formatting—as this would rightly fail DKIM. Also, check server logs to find any issues on the sending side during the signing process or concerns on the receiving end.
- You can also contact your DNS or email provider’s tech support for a more precise diagnosis. Sometimes, a version upgrade is necessary due to system dependencies, or security enhancements need to be rolled back to ensure DKIM lookups aren’t prevented from running.
Once you’ve completed all of the above in an orderly fashion, you’ll be able to troubleshoot and verify that your DKIM settings will function for optimal email security and deliverability.
Combine Warmy and DKIM setup to achieve optimal email deliverability
Using Warmy’s free email deliverability tool
The free email deliverability tool from Warmy provides a thorough approach to confirm SPF and DMARC settings in addition to DKIM. This is what to anticipate from utilizing this tool:
- Warmy verifies the multi-aspects of your domain, including DKIM, SPF, and DMARC configuration. It confirms these records’ existence and accuracy in your DNS configuration.
- Email deliverability insights, including what percentage of your emails are ending up in spam. This can point to problems that could be hurting the way your emails work.
- Blacklist monitoring. Warmy will also look up whether your domain is on any email blacklists, which might have a big negative effect on your deliverability.
Using a program like Warmy can give you a thorough picture of your deliverability and security status, enabling you to decide how best to tailor your email campaigns.
Comprehensive overview of your domain health

Warmy’s Domain Health Hub is unlike any you’ve ever seen. It provides a domain-level health dashboard so businesses and senders can strategize more precisely.
The Domain Health Hub includes the following features:
- A domain health score based on factors like authentication, blacklist status, and inbox placement tests.
- Weekly or monthly tracking of spam rate trends and overall deliverability performance
- Comprehensive DNS status checks to easily validate SPF, DKIM, DMARC, rDNS, MX, and A records for stronger authentication & security.
- Optimized multi-domain monitoring for easier monitoring and identification of issues
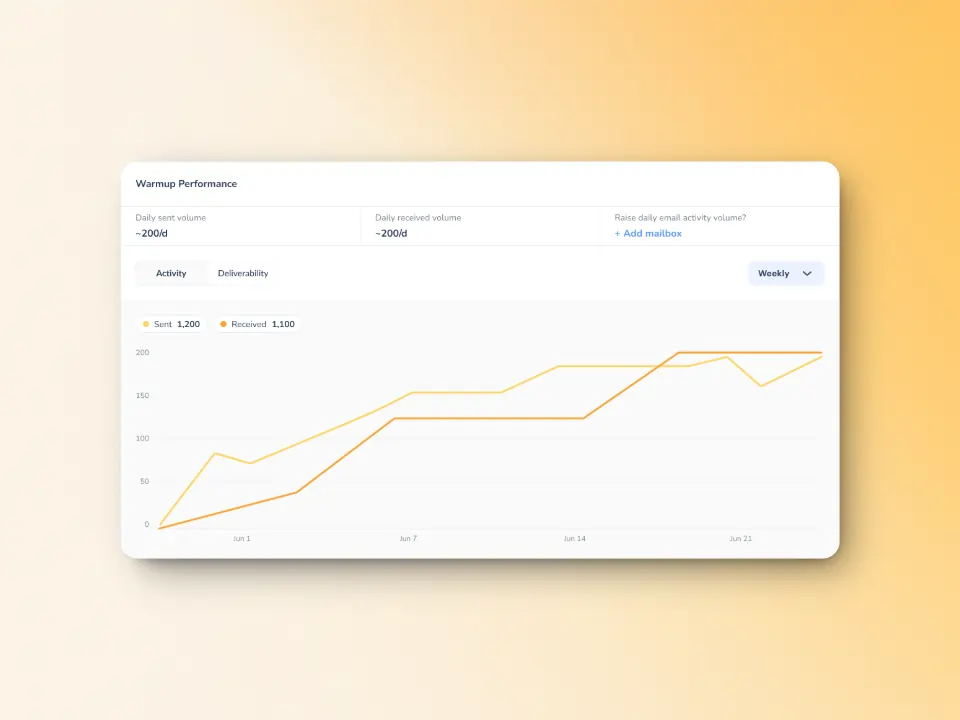
While improving the deliverability and security of your emails depends critically on correctly implementing DKIM, that’s only one aspect of the process. Warming up your email is essential to really maximizing the success of your email outreach, particularly for new or seldom used email addresses. Through this procedure, the amount of emails sent is progressively increased, which helps to build a reputation as a reliable sender with Internet Service Providers (ISPs).
Warmy offers a sophisticated platform to assist with this process. The platform not only streamlines the warmup process, but also maximizes your email deliverability through intelligent sending practices. This approach minimizes the risk of your emails landing in spam folders, thereby improving overall engagement rates.
Here’s how Warmy does it:
- Automatically yet gradually increases sending volume to build trust with various mailbox providers.
- Simulates real human-like interactions—emails are opened, replied to, and marked as important, boosting deliverability.
- Works across 30+ languages so your emails look natural and relevant for global audiences.
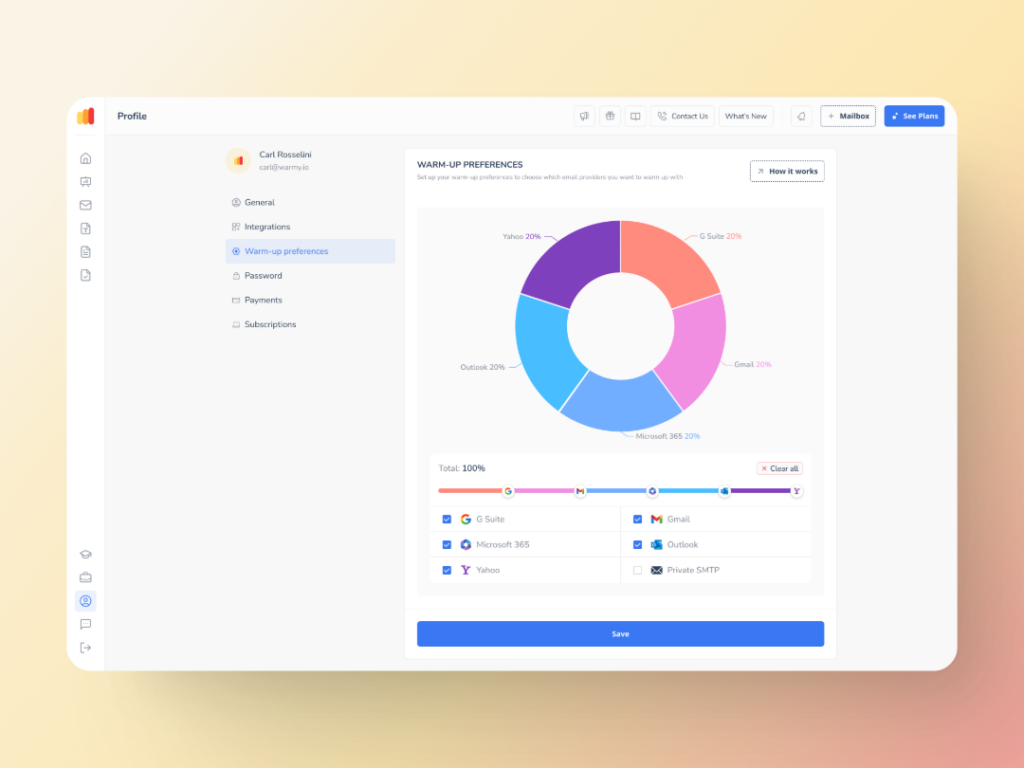
Enhanced warmup process through customization
The Warmup Preferences feature empowers senders to take full control of their warmup process. For example:
- Senders can customize the warmup distribution across GSuite, Gmail, M365, Outlook, Yahoo, and even Private SMTP.
- Senders can tailor engagement patterns and choose between B2B or B2C customers.
Senders can also set the warmup settings across all mailboxes at once, or one by one.
All settings can be changed directly from within the Warmy system.
Advanced seed lists for real engagement
Warmy.io’s advanced seed lists contain genuine email addresses which pave the way for authentic email interactions (opens, scrolls, clicks, replies, archives)
If an email lands in spam, it is removed and marked as important.
Using these advanced seed lists result in better recognition by ISPs like Google, Microsoft, and Yahoo—which translate to improved sender score and overall reputation.
Currently Warmy has seed lists for Gmail, Outlook, and Yahoo..
Learn more about Warmy’s seed lists here. Or, check out our additional resources:
Conclusion
Any company trying to enhance its email security and deliverability will find many advantages in setting up DKIM (DomainKeys Identified Mail) in Office 365. Businesses who use DKIM make sure their emails are validated, which lowers the possibility that their messages will be reported as spam. This not only makes their messages more credible but also stops email spoofing from being utilized on their domain.
Adding DKIM to Office 365 is a simple but effective way to protect the email ecology of a company. DKIM is essential to preserving the integrity and dependability of email communication since it confirms that emails are actually from the domain they state to be from and have not been altered while in route.
While implementing DKIM is no doubt a tested and proven strategy to improve email deliverability, it is not the only factor that can make or break your email strategy.
Warmy gives email senders an inside look into the inner workings of email deliverability. Try it out for free (seven days—no credit card required), or book a demo with an expert for a more personalized walkthrough.
📜 Related articles:











