In the world of emails, getting your message seen is just as important as crafting the perfect copy. But even the most well-written email is worthless if it never makes it to the inbox. That’s where email warm-up and authentication come into play—and why understanding their intersection is no longer optional.
However, the email landscape continues to become even more complex. Security standards are tightening, legacy protocols are fading, and mailbox providers are smarter—and stricter—than ever. This means the rules around how emails are sent, authenticated, and received are shifting fast.
This research report was born out of that complexity. It blends Warmy’s internal findings with official documentation and real-world email infrastructure trends to give you a clear, up-to-date view of what’s happening behind the scenes—and what you need to do to stay ahead.
The premise: Understanding inbox warmup and email deliverability
Inbox warmup is the practice of gradually building trust with mailbox providers. Think of it like building credit. When you open a new bank account or get a new phone number, you don’t immediately start making large transactions or calling hundreds of people. You build a track record first.
Warmup works the same way for email. By starting with low sending volumes and slowly increasing activity, your email address begins to appear more legitimate in the eyes of spam filters. A proper warmup process includes opening emails, replying to them, marking them as important, and even removing them from spam folders. These behaviors signal positive engagement, helping email providers recognize that your messages are wanted, trusted, and safe.
A lot of senders don’t completely understand how sender reputation influences inbox placement—thus, they don’t invest in the warmup process.
Q: How does warmup impact sender reputation?
A: It’s a score mailbox providers use to decide whether to deliver, delay, or drop your email. A new domain or mailbox starts with zero reputation, making it highly susceptible to being flagged or filtered. Inbox warm-up helps build that reputation from scratch.
🔖 Related Reading: Importance of Email Warmup before Cold Outreach
The better your sender reputation, the higher your chances of landing in the inbox. But reputation isn’t built on sending volume alone—it’s shaped by consistency, engagement, and authentication.
Key drivers of email deliverability
Here are the three pillars that determine whether your email reaches the inbox or the void:
- Sender reputation: Track record of sending wanted emails with low spam complaints. Newer domains or IPs have no reputation yet, so warmup comes in to help them establish a track record.
- Email authentication (SPF, DKIM, DMARC): Proper DNS records help establish your domain’s emails. Without them, your emails may be flagged as suspicious—even if they are legitimate. Warmup is more effective when emails are authenticated.
- Engagement signals and interactions: Engagement builds trust, and this pertains to open rates, replies, low bounce rates, and emails marked as important. Warmup services simulate positive engagements to build sender reputation.
The legacy challenge: POP3 and MFA in today’s security landscape
Despite all the advancements in email security and identity management, legacy protocols like POP3 and IMAP are still alive and kicking. Why? One word: compatibility.
Q: What is POP3 and what is IMAP?
A: POP3 (Post Office Protocol 3) and IMAP (Internet Message Access Protocol) are protocols used by email clients to pick up messages from a mail server. POP3 downloads emails and typically removes them from the server, while IMAP keeps emails on the server and syncs across multiple devices, allowing for better access and management.
These protocols were developed decades ago. Replacing or rewriting them entirely would break a lot of infrastructure overnight.
So what are the challenges related to POP3 and MFA? Here’s a quick overview:
- POP3 and IMAP use basic authentication (username and password), which doesn’t support Multi-Factor Authentication (MFA).
- MFA-enabled accounts can’t log in via POP3/IMAP without a workaround, often causing login failures.
- Disabling MFA to maintain access is a major security risk.
- App passwords are one-time generated codes that bypass MFA and allow access to legacy protocols.
- Warmy.io recommends using 2FA with app passwords for secure mailbox warmup.
- While app passwords work, they are sometimes considered less secure by providers.
In short: legacy protocols are a necessary bridge for now, but they must be handled with care—especially when security and deliverability are on the line.
OAuth vs. legacy access: what today’s senders need to know
To overcome the limitations of basic username/password logins, the email industry has widely adopted OAuth 2.0—a modern, secure way for apps to access your account without ever seeing your actual password. Instead, the app is given a token that tells it it is allowed to do certain things, like send or read emails.
Building on this, OpenID Connect (OIDC) adds identity verification and provides for Single Sign-On (SSO) with platforms like Google Workspace, Microsoft Azure AD, and Okta. It’s the new normal for many businesses.
Why it’s not always simple
While OAuth and OIDC offer strong security, they’re not always easy to use—especially for warm-up platforms that automate inbox connections. Unlike passwords, OAuth requires:
- A browser-based login
- User approval
- Sometimes, admin permissions
This works for one-time logins, but it’s harder to scale across many accounts or automate in scripts. That’s why some platforms still use IMAP + app passwords when OAuth isn’t available or practical
Why legacy access still exists
If OAuth is so great, why do we still need legacy methods? Mainly because of compatibility and real-world constraints:
- Older devices (like printers) can’t handle OAuth flows.
- Command-line tools and scripts often can’t trigger web-based logins.
- Corporate policies may block third-party apps from using OAuth without approval.
So, providers like Google and Microsoft have adjusted:
- Google ended “less secure app access” but still allows OAuth or app passwords.
- Microsoft disabled basic auth but supports OAuth 2.0 for IMAP/POP.
What this means for Warmy users
As a Warmy.io user, here’s what you need to know:
- Use OAuth whenever available. It’s secure, doesn’t expose your main password, and can be revoked or scoped down easily.
- App passwords are still valid for certain use cases but must be created with caution and revoked when not needed.
- If there is a “Connect with Google” or OAuth-based login, take it—it’s the safest path.
- Never share your main password or disable MFA — that’s a red flag.
Ultimately, modern authentication is the future—but the ecosystem hasn’t fully caught up yet. Until then, a hybrid approach remains necessary. Use modern auth when possible, and if you fall back to legacy access, do it safely, with clear expiration plans and strong account protection in place.
Email forwarding, SPF, SRS, and DMARC explained
Forwarding emails—like sending your work emails to Gmail—may seem harmless, but it can quietly break authentication protocols and hurt your deliverability. The main issues? SPF fails, and DMARC might reject the message, even if it’s legitimate.
Why forwarding breaks SPF and DMARC
- SPF checks if an email is coming from a server authorized by the sending domain.
- When an email is forwarded, the forwarder’s IP is now sent on behalf of the original domain—but that IP isn’t listed in the domain’s SPF record, so SPF fails.
- DMARC requires SPF or DKIM to pass and align with the visible “From” address. If SPF fails and DKIM isn’t valid, DMARC will also fail, and the email may be rejected.
To fully understand this, we need to answer the following question:
Q: What is SPF and DMARC?
A: SPF (Sender Policy Framework) is an email authentication standard that lets domain owners specify which mail servers they use to send the email. This checks whether the sender’s IP address matches the domain’s published SPF record to stop spoofing. DMARC (Domain-based Message Authentication, Reporting, and Conformance) uses SPF and DKIM as building blocks, publishing a policy that requires alignment between the sender’s visible “From” address and the domains authenticated by SPF or DKIM. It also enables domain holders to publish policies (such as reject or quarantine) and reports on authentication outcomes.
🔖 Related Reading: SPF, DKIM, and DMARC: Boosting Email Security and Deliverability
How SRS helps fix the problem
- SRS (Sender Rewriting Scheme) solves the SPF issue by rewriting the envelope sender. So instead of: alice@bank.com, you get: SRS0=alice=bank.com@forwarder.com
- Now SPF checks pass, because the domain matches the forwarder’s IP. However, this breaks DMARC alignment, which means DKIM must step in to save the day.
- If DKIM is working and aligned, the forwarded message will still pass DMARC. But without SRS or DKIM, you’re looking at a failed delivery.
A better alternative: skip forwarding
Many deliverability experts recommend skipping forwarding altogether and using direct retrieval (like POP3 or IMAP) instead. Here’s why:
- Gmail or your warmup platform pulls the email directly from the original inbox.
- This keeps SPF, DKIM, and DMARC intact, since there’s no re-sending involved.
While it requires app passwords or credentials, authentication remains reliable.
What Warmy users should know
If you’re using forwarding, keep these best practices in mind:
- Use SRS if your forwarding provider supports it (e.g., Office 365).
- Make sure DKIM is properly set up on your domain.
- Be cautious with strict DMARC policies (p=reject) during warmup—consider p=none or p=quarantine.
- Whenever possible, choose POP3/IMAP retrieval instead of forwarding.
- Follow Warmy’s connection instructions to avoid deliverability issues caused by authentication mismatches.
The role of DKIM in authentication and forwarding
How DKIM works
DKIM (DomainKeys Identified Mail) adds a cryptographic signature to your emails, proving they came from your domain and weren’t altered in transit. The signature is created using a private key on your mail server, while the public key is stored in your domain’s DNS.
When a receiving server checks the email:
- If the signature matches and the message is unchanged, DKIM passes.
- If the content was modified (even slightly), DKIM fails.
Why DKIM matters in forwarding
Unlike SPF (which often fails when an email is forwarded), DKIM stays intact—as long as the content isn’t changed. That makes it a critical fallback for forwarded messages.
If the signing domain matches the visible “From” address, DKIM can help your message pass DMARC, even when SPF fails. That’s why properly aligned DKIM is essential.
DKIM and deliverability
Spam filters like SpamAssassin use DKIM as a positive signal. For example:
- DKIM_VALID – Signature is valid
- DKIM_VALID_AU – Valid and aligned with the sender’s domain
- DMARC_PASS_REJECT – DKIM helped pass a strict DMARC policy
Even small boosts in trust can help your email avoid the spam folder—especially when inbox placement is borderline.
While powerful, DKIM has some limitations:
- If the message is altered in transit, the signature can break.
- It doesn’t evaluate content quality—even spam can pass DKIM.
- Replay attacks are possible if a signed message is reused.
Still, DKIM is one of your best tools for authentication—especially in forwarding scenarios where SPF can’t be trusted.
The limitations of SPF, DKIM, and DMARC
What these protocols do and don’t do
SPF, DKIM, and DMARC are not spam filters—they’re ID checks. They confirm that an email was sent from a legitimate source and hasn’t been tampered with, but they don’t evaluate content, reputation, or user trust.
Think of them like showing ID at a club door:
- SPF checks if the sender is allowed to use a domain.
- DKIM verifies that the message wasn’t changed in transit.
- DMARC makes sure the domain in the “From” address matches the one authenticated by SPF or DKIM.
But none of them decide whether the message is actually wanted. That’s the job of spam filters and reputation systems.
While these standards were created to tackle specific problems like spoofing of sender identity, they are not magic bullets that stop all unwanted emails or spam. They are authentication tools—not authorization or spam filters.
How spammers still get through
Spammers are getting smarter. Instead of spoofing brands, many now register their own domains and set up valid SPF, DKIM, and DMARC records.
These emails will then pass the checks because the “spammer” is technically the legitimate owner of the domain they’re sending from. So they aren’t spoofing other senders. While the email authentication systems can confirm the mail is indeed from a legitimate domain, it is up to reputation systems and content filters to decide that the email is spam.
Common weaknesses to watch for
Here’s a clean and easy-to-read table summarizing the key limitations and considerations:

Key takeaway: Just because you set up SPF, DKIM, and DMARC properly, all your emails will go to target inboxes. There are many other factors at play. Authentication is just the first step. You need to follow through with your reputation.
Additional techniques for improving reputation
While SPF, DKIM, and DMARC are essential, mailbox providers go beyond them. They also check your infrastructure and behavior to determine if your emails are trustworthy. Two lesser-known—but important—factors are DNS configuration and SMTP delay handling.
DNS resolvability checks
Before even looking at your message, mail servers may verify:
- If your IP has a valid PTR (reverse DNS) record.
- The domain name resolves back to your IP (forward-confirmed rDNS).
- Your HELO/EHLO hostname is valid.
- Your MAIL FROM domain has valid DNS (MX or A record).
If these checks fail, your email might be rejected or deprioritized—especially if the domain looks fake or newly registered.
What to do:
- Set proper PTR records.
- Use resolvable hostnames.
- Avoid sending from domains without complete DNS setup.
SMTP delays and anti-spam tactics
Mailbox providers use delays to detect bad senders:
- Greeting delay: Pauses before the SMTP welcome message to catch impatient spam bots.
- Greylisting: Temporarily rejects the first message from unknown senders—legit servers retry, spam bots often don’t.
- Slow responses: Slows down bulk spammers without affecting patient senders.
What it means for warmup:
- Early messages may be delayed—this is normal.
- Warmy and other trusted tools handle retries smoothly.
- Poorly built systems may give up too soon or trigger spam defenses.
How Warmy.io helps with the battle for authentication
Strong email deliverability depends on more than just passing SPF, DKIM, and DMARC. You also need to show consistent, human-like engagement—opens, replies, and behavior that mailbox providers trust.
That’s where Warmy.io truly shines: combining authentication with smart, automated warmup to build and protect your sender reputation.
Free SPF and DMARC Record Generator
Setting up authentication can be tricky—but Warmy makes it simple. Our built-in generators help you create free SPF records and free DMARC records tailored to your domain setup. This ensures you start off with proper alignment and avoid costly mistakes that lead to spam folders or bounces.
AI-powered email warmup to establish your sender reputation
Even with proper authentication, a poor sender reputation can still send your emails straight to spam. That’s why email warm-up is critical—it helps build credibility with mailbox providers before you start sending at full volume.
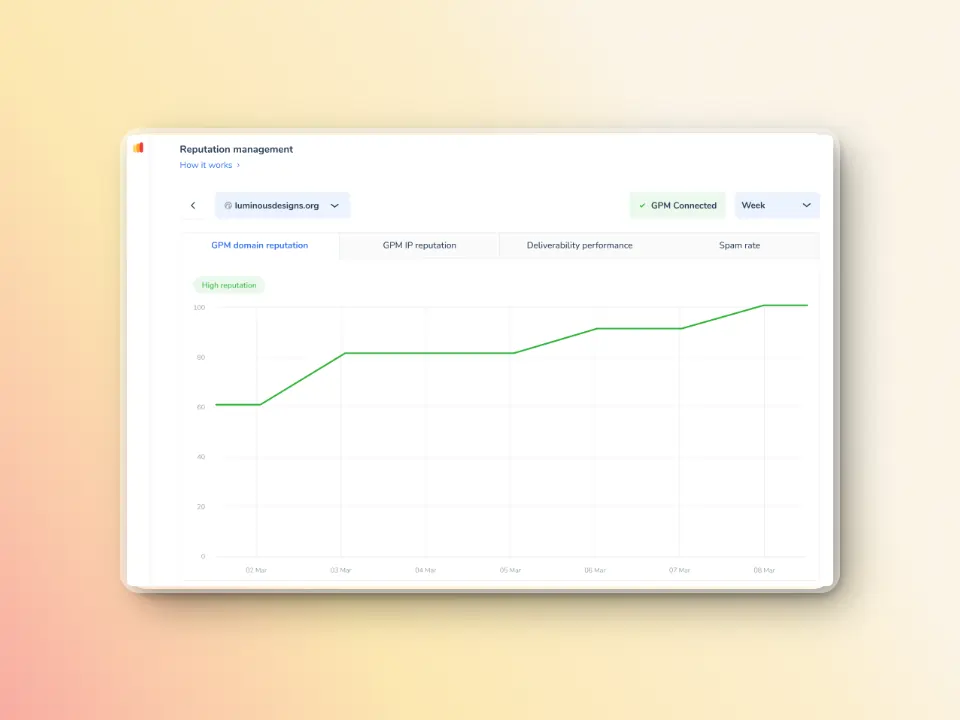
New domains, in particular, need a careful introduction. Sending too many emails too quickly can raise red flags, trigger spam filters, or even land you on blacklists. And once engagement drops—due to bounces or low open rates—your reputation takes a hit, making things worse over time.
How Warmy.io’s email warmup helps:
- Gradual volume increase to safely build trust with mailbox providers.
- Simulated human engagement—emails are opened, replied to, and marked as important.
- Multi-language support (30+ languages) so your warm-up emails feel natural and regionally relevant.
In short: Warmy helps you earn trust before you scale—so when your real campaigns go out, they land in inboxes, not junk folders.
Enhanced email warmup with Warmy.io’s advanced seed lists
Warmy offers the most advanced email seed list. It offers actual engagement. Your emails are opened, scrolled through, clicked on, and replied to. If there are emails that land in spam, these are removed and marked as important to let the ESPs know you are credible.
If you’ve been using Warmy’s Established Email Seed List for a while now, then you already know it’s not just another seed list—and it just keeps getting better.
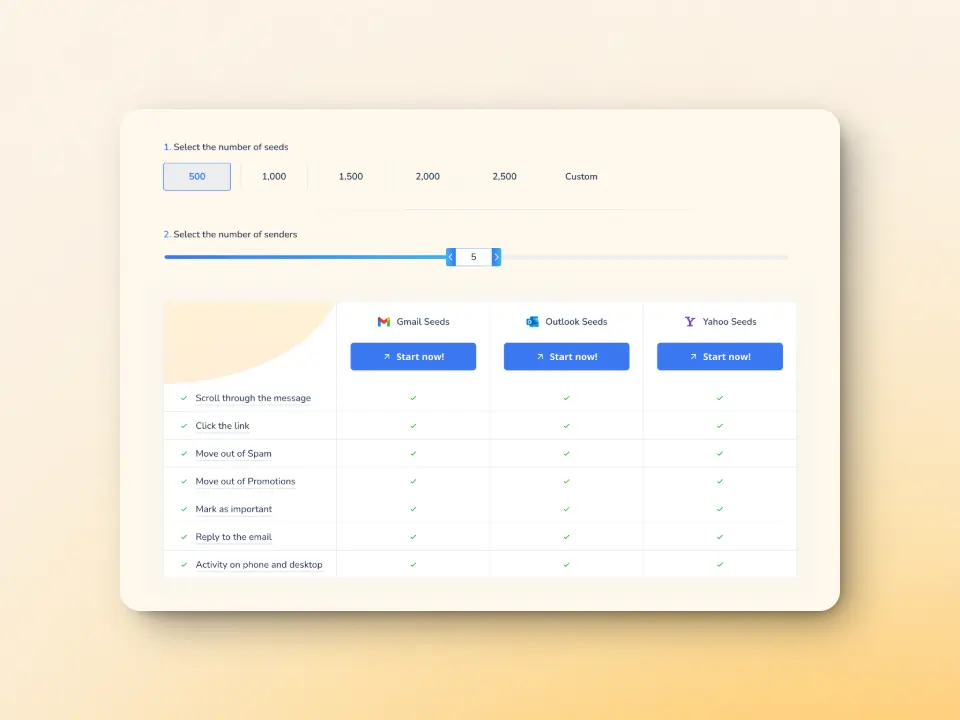
Warmy has recently introduced the API Endpoint for Established Seed List—a new way to access, manage, and configure your seed list splits directly from your system. This means there are no more manual updates, and no more time wasted with the following capabilities:
- Seamless integration with real-time seed list data that goes straight into your system with API access.
- Efficiency boost via automated split management which reduces errors, and saves valuable time.
- Better inbox placement due to properly configured splits mean fewer bounces and stronger sender reputation.
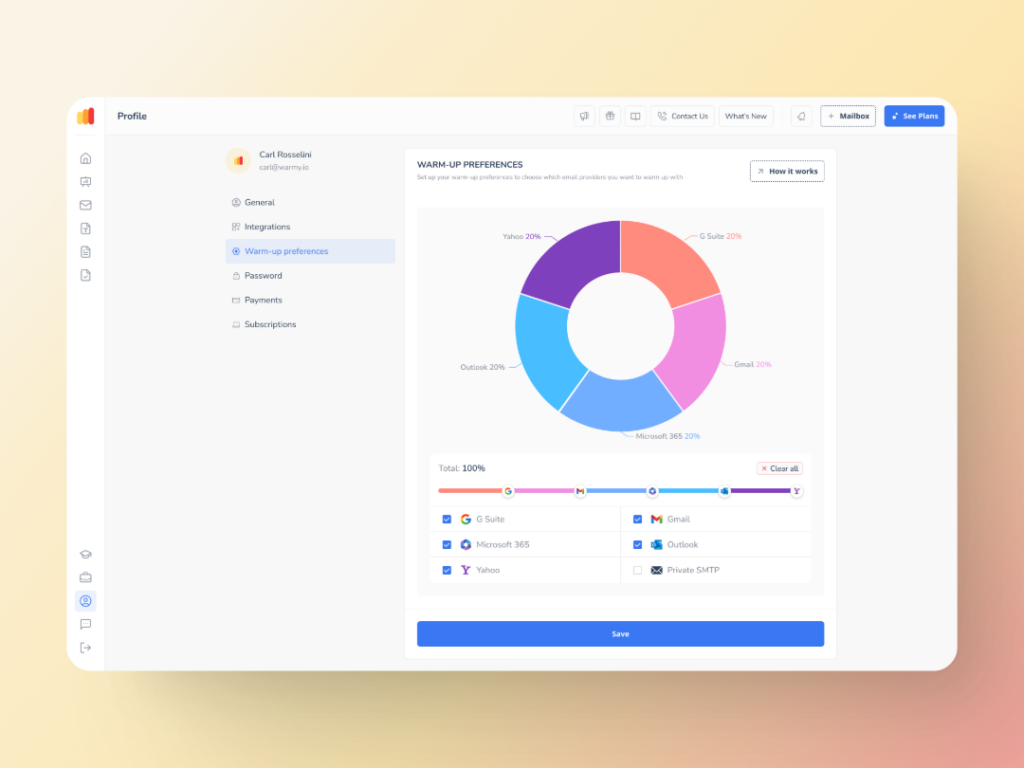
Customizable Warmup Preferences
Warmup Preferences senders customize and fully control the warmup process from both sender and user levels.
- Customization of warmup distribution across GSuite, Gmail, M365, Outlook, Yahoo, and even Private SMTP.
- Choose between B2B or B2C customers when it comes to engagement patterns.
- Set warmup settings for all your mailboxes at once—or even one by one, whichever you prefer.
- All settings can be changed directly within Warmy’s system, so there’s no need to contact support and wait
- Define percentage of emails that will be sent to each provider
Complete visibility into all aspects of your email deliverability
Our free email deliverability test offers a full diagnostic of how your emails perform and where they land.Here’s what you get:
- See how many of your emails land in the inbox, spam, promotions tab, or go unreceived—so you know exactly where you stand.
- Find out if your domain or IP is on any major blacklists and get ahead of reputation issues with early alerts.
- Get instant feedback on whether your SPF, DKIM, and DMARC records are correctly configured and passing.
Additionally, the Domain Health Hub provides a smarter way to monitor various aspects of your deliverability so you know which points you need to focus on. Here’s what it includes:
- Domain health score: A dynamic score built from multiple signals—authentication, blacklist status, inbox tests, and spam rate trends.
- Weekly or monthly performance tracking: Track how your deliverability evolves over time and spot issues before they affect your campaigns.
- Comprehensive DNS status checks: Instant validation for SPF, DKIM, DMARC, rDNS, MX, and A records to ensure your infrastructure is correctly set up.
- Multi-domain monitoring: Manage and compare the health of all your domains from one centralized dashboard.
- In-depth reports & metrics: Drill into each domain’s performance with detailed analytics and suggestions for improvement.
Combine authentication and warmup for deliverability success
Warmy doesn’t just warm up inboxes—it builds your domain’s reputation from the ground up. By aligning strong authentication with strategic warm-up and engagement, you create the trust mailbox providers are looking for.
Ready to go deeper?
Download the full report to explore all the best practices, expert insights, and actionable tips to boost your email deliverability from day one.











